In today’s connected world, access to Wi-Fi is a necessity. Players in the hospitality industry are expected to offer Wi-Fi access to their guests during their stay at their facilities for a connected experience. There are several technology companies across the globe that are enabling digital transformation in the travel and hospitality sector with numerous offerings that help design, develop and deploy an effective WiFi services management solution.
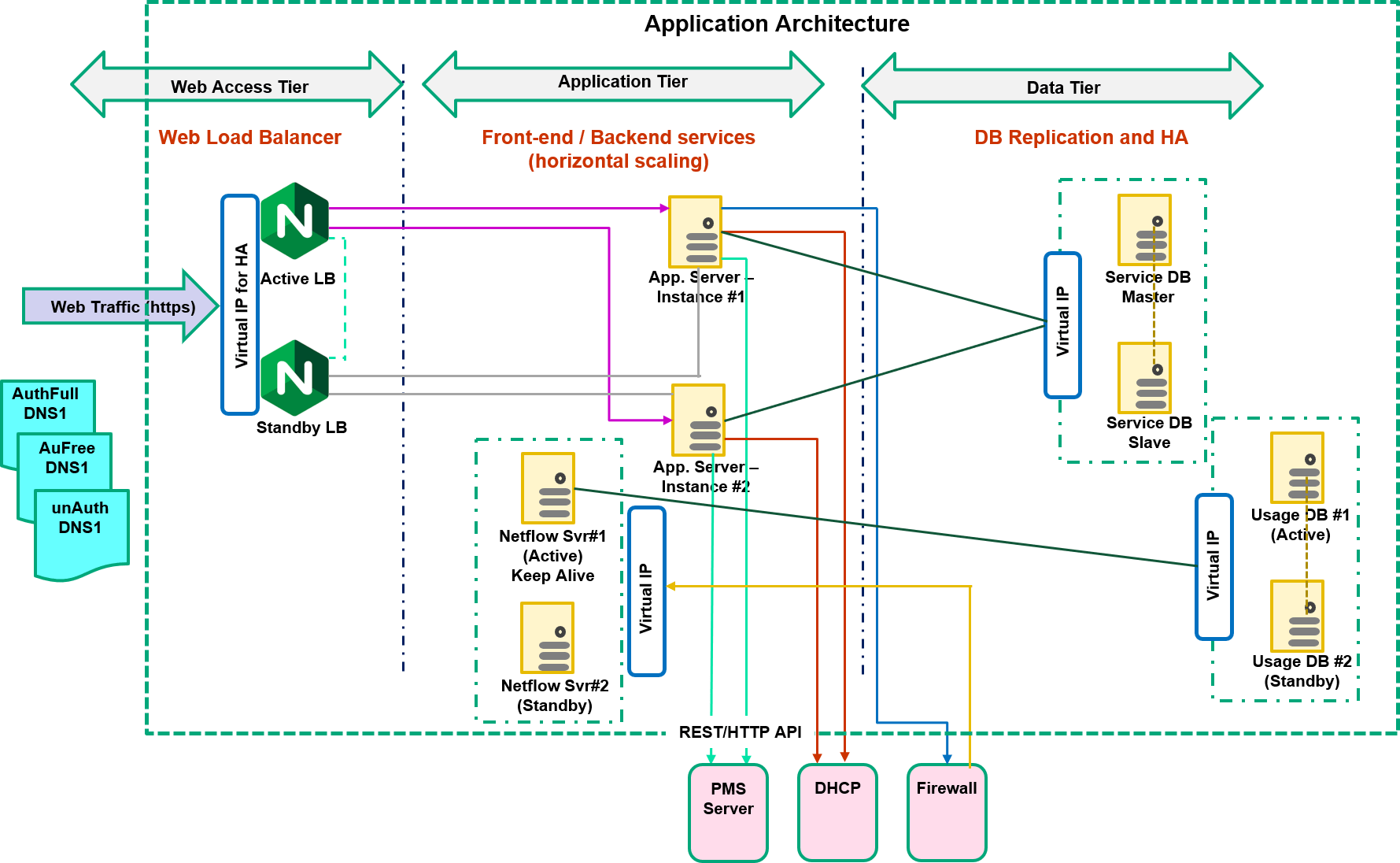
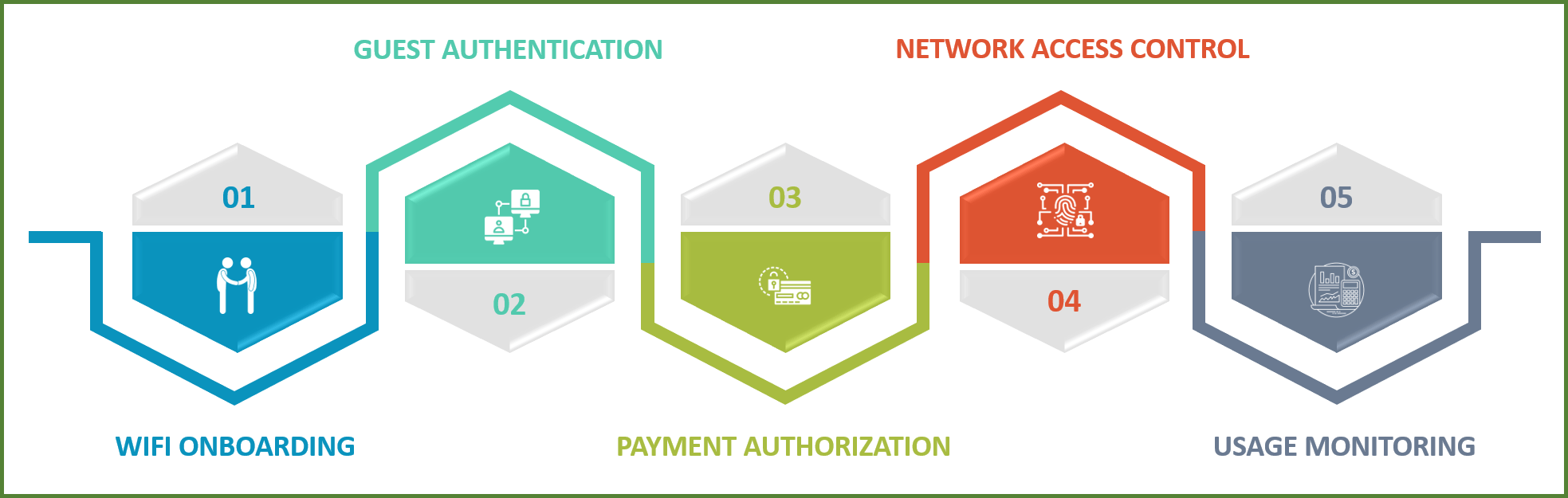
Some of the processes involved in Wi-Fi Service Management that are integral to providing a seamless guest experience are shown in the diagram below:
Wi-Fi Onboarding
The single most important objective of a Wi-Fi service management solution is to enable Wi-Fi access for the guests with minimum friction. Here are some of the steps that have been implemented to ease the onboarding process:
- The guests should not be required to go through one more registration to use the service. He/She should be able to use their room number as the login credentials to access the network.
- Alternatively, the guest should be able to use a pre-shared Weblink/URL (shared at the time of reservation). The guest can download and install a profile on their device before they travel to the hotel property. When the guest enters the premise using such a device, the guest is seamlessly on-boarded on-to the Wi-Fi network thereby eliminating the need for the user to select an SSID or go through a login process. The user credentials embedded in the profile are used for authentication in the background providing a frictionless Wi-Fi onboarding experience to the user.
- Once the guest logs into the network using a given device, the system remembers the device for the entire duration of the stay and does not require the guest to login again.
In addition, the first interaction with the Wi-Fi management solution is considerably simplified by the presence of a captive portal splash page. All smart phones have a built-in captive network detection mechanism. These phones try to reach specific “connectivity check” websites and expect to get a specific response. Depending on the response, the phone is redirected to a web portal and presented a captive portal splash page. The presented captive portal page then can be used to implement work-flows for facilitating login and plan purchase.
Guest Authentication
As with any private network, Wi-Fi service providers want the guests to be authenticated before accessing the Wi-Fi network. This allows the providers to identify the users in case of violation of the “usage terms and conditions”.
The guest is required to enter login credentials while accessing the Wi-Fi network. In this case, the login credentials are an easily memorized guest information such as the room number and an easy passcode. For instance, the date of birth provided at the time of reservation can potentially serve as a passcode for authentication. The existing Property Management System (PMS) is used for authenticating the guest’s input. The integration with PMS for authentication is easily done using RESTful APIs.
Payment Authorization and Plan Activation
Users are provided with a variety of paid plans depending on their needs. The options include a per-day plan or entire-stay plan, one-device plan or multi-device plan etc. Both post-paid and pre-paid options are supported.
The guests with pre-paid plans are identified by the back-end system (PMS) during the login workflow. On determining that a guest is provisioned with a pre-paid plan, the Wi-Fi service management system asks the guest to redeem the plan without having to go through any payment authorization work-flow.
The back-end system i.e. the PMS maintains a folio for each guest. This is done to keep track of the services purchased by the guest. For the guests who want to be billed later, the Wi-Fi service management requests the back-end system to add a charge against the guest’s folio. The Wi-Fi service management system activates the plan on either verifying a presence of a card on file or on successful payment authorization of a card presented during the process.
The integration with the backend system (PMS) for the payment authorization is again done using RESTful APIs.
Network Access Control
For any enterprise network, the enforcement of appropriate access control is important. Multiple levels of network access controls are supported in the system.
- No Internet access: This policy is associated with users who have not logged into the system. For such users, web traffic is redirected to login page and the user is asked to go through the login workflow.
- Limited Internet access: This policy is associated with users who have logged into the system. For such users, access is set to a group of white-listed Internet sites in addition to the Intranet. Example of whitelisted sites could be airline website allowing users to print their boarding passes.
- Full Internet access: This policy is associated with users who have a paid Internet plan. For such users, full Internet access is allowed except for sites blocked per the network policy. For example, gambling sites may be restricted at some places or streaming sites may be restricted on aircraft.
The access control can be enforced on a per-user basis. The access control policy is employed by enforcing control over the existing networking equipment. Integration with network equipment is done using RESTful APIs. Some network equipment have an upper limit on the rate of API calls in the management plane. The solution was designed to do a bulk policy assignment so as not to breach this limit potentially causing problems in service.
Usage Monitoring
Monitoring of network usage is useful for multiple reasons:
- Tracking per-user data transfer (upload/download) and enforce per day/ per user limits
- Monitoring the aggregate data transfer and accordingly plan the back-haul capacity
- Marketing teams like to monitor the number of active devices per user and offer optimal plans
The current Wifi Service Management systems implement monitoring based on the Netflow data exported by networking equipment.
Conclusion:
The above cites some of the use cases that can be implemented with WiFi Service Management systems developed by HSC. HSC has a rich experience in BSS & OSS technologies which helps us understand an operator’s business requirements and provide them customized solutions.
Reach out to us to understand how we helped set up an end-to-end WiFi Service Management system for a leading hospitality business.

Product Engineering Services Customized software development services for diverse domains
Quality Assurance End-to-end quality assurance and testing services
Managed Services Achieve scalability, operational efficiency and business continuity
Technology Consulting & Architecture Leverage the extensive knowledge of our Domain Experts