Every equipment manufacturer requires a solution for the element management of the equipment. Traditionally, an EMS is built custom to the requirements of the network elements that it has to manage. When the equipment manufacturer builds a new product line or upgrades the existing one, the cost to port / re-engineer the existing EMS becomes a major hurdle for the change.
Reusable NM Components (RNMC) provides an easy solution to this problem. RNMC is based on basic understanding that each EMS has few generic needs along with specific requirements of network elements. These generic needs are; management protocol based messaging, handling alarms and events, logging and tracing, persistence, access-controlled GUI, and maintaining audit logs. Whereas specific needs are based on custom GUI for provisioning and statistics monitoring.
RNMC provides a set of reusable components that support these generic needs and are extensible enough to plug-in specific behavior into them.
The emerging technologies are resulting in the expansion of the telecom network at a fast pace. This expansion calls for a significant effort to provision, manage and monitor this network. There is always a challenge to maintain this network so as to provide uninterrupted services to the end user and stay ahead in the competition.
NMS, EMS and OSS provide the answer to these goals. But there are numerous challenges faced in the development of these solutions. Some of the challenges are:
All of the Telecom Service Providers are having some NM solution to manage their existing networks. And whenever there is a new product line in their network they need to enhance their existing NM solutions. So, which standard approach and specifications to follow to develop these systems such that if needed the components of the systems are reusable and in a short time, with a minimalist effort and inexpensive way they are ready to support multi-technology systems?
Building an NM solution from scratch requires a lot of effort and basic modules present in common software applications. Moreover, the turnaround time to build such a system is large and is bound to result in a loss of the prospective business for the customer.
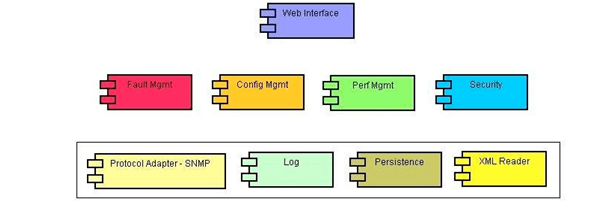
The RNMC aims at providing the common components those are required to build any software application and the basic components of an NM system by strategically selecting the freeware (those are best-in-industry third party products) and building components on the top of it. Its support for Fault, Configuration, Performance and Security Management is geared to a high degree of customization and extension with minimal coding. This enables the use of the developed components to build an NM solution with FCAPS capabilities in a quick and inexpensive way.
In order to build a new EMS using RNMC, first an appropriate protocol adapter needs to be plugged into the components. Then few custom handlers are prepared to address specific requirements of a network. These custom handlers are plugged into the predefined hooks of RNMC, through XML files. (This is facilitated by Java reflections). Then custom screens are built for configuration & performance parameters for the network elements, and are plugged into the CM & PM components. This builds the complete EMS. RNMC facilitates a web-based interface for operators.
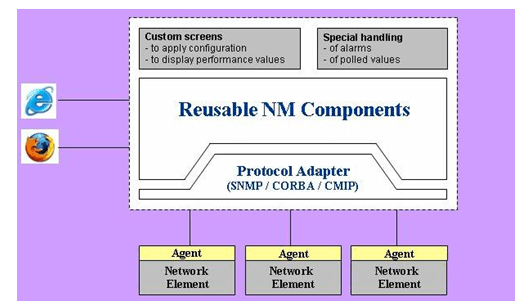
All the best-in-practice Object Oriented Design principles and it is ensured that there is a loose coupling in the architecture layers. Thus, the developed independent client and server modules ensure that selective module can be deployed those are required in a specific NM implementation.
The components have been developed using Java technologies which ensure that it runs on multiple platforms.
Multiple Database and ORM tools Support
Default Hibernate template support from Spring framework is used as an ORM interface for implementing the data access object layer ensuring that it is compatible with any RDBMS. Default Hibernate support can be replaced by any other template implementation by plugging it in Spring framework.
RNMC is capable to meet the requirements of any NM implementation with the support of its highly customizable and extensible features. The components are customizable using XML based configuration files. Extensions are possible as the plug-in feature for customizable hooks is also provided, i.e., if an application requires to deviate from or enhance the feature provided it can be achieved with a minimal code effort by using the Java API provided and an XML configuration for the same.
RNMC Protocol Adaptation Layer encapsulates all the protocol specific implementation and ensures support to any of SNMP, TL1, CLI, CMIP or CORBA protocols thus enabling the management of multi-technology and multi-vendor systems. Presently, it supports SNMP v1, v2c traps and notifications.
A support for HTTP based web client is provided. The latest MVC framework Struts2 has been exploited to develop this web client. HTTPS access to the application via the web client is also supported. But interface between frontend & backend components is very loosely coupled and the frontend developed using any other technology can also be plugged with the existing backend components.
This component is responsible for receiving the events and alarms from the managed network, logging them in the persistent storage and reporting them in a presentable format to the NOC operators.
Key features of Fault Management are:
Business benefits those can be realized by Fault Management are:
This component is responsible for provisioning of network elements. It takes values for configurable parameters, stores it in local database, and applies them on the network element.
Key features of Configuration Management are:
Business benefits those can be realized by Configuration Management are:
This component is responsible for providing the Authorization, Authentication and Auditing functions.
Key features of Performance Management are:
Business benefits those can be realized by Performance Management are:
This component is responsible for providing the Authorization, Authentication and Auditing functions. Key features of Security Management are:
Business benefits those can be realized by Security Management are: